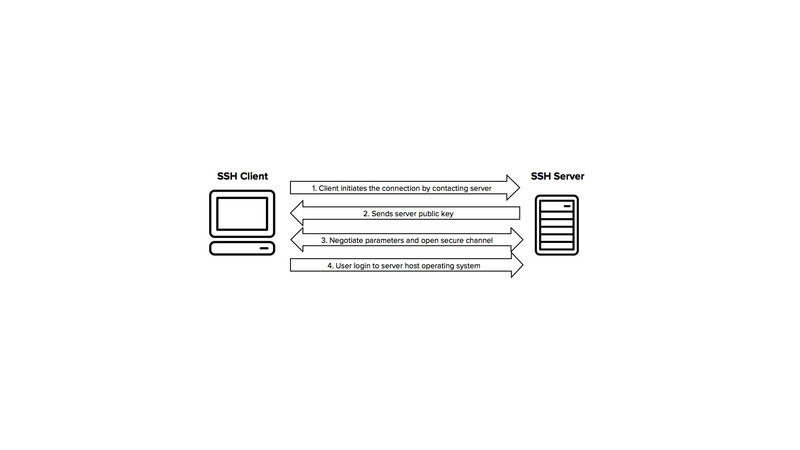
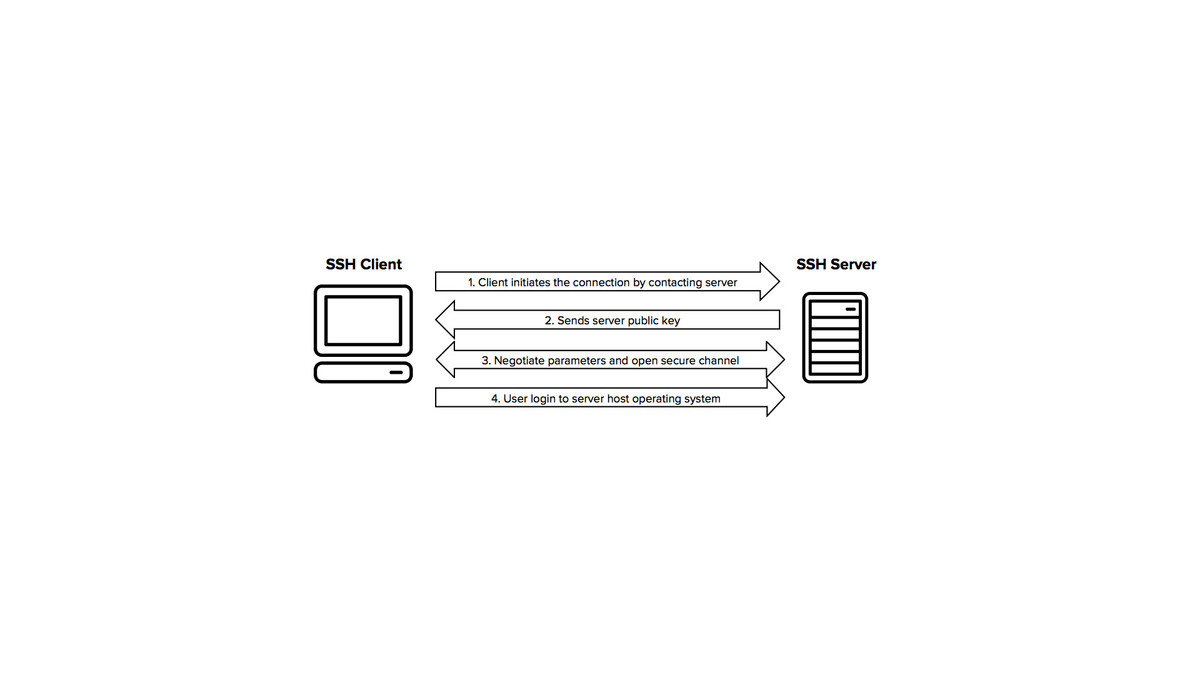
Connection reset by peer — ssh sshfs error
+ Add to Google News
- Tutorial
- en
- Mirela
- 4 years ago
- 2021-08-09 08:00:00
- comments
- : 2 minute 29 secunde
- image: ssh
Recently, after re-installation of Ubuntu Linux, sshfs mount, from a Fedora Core, has failed with the following error message, read: Connection reset by peer.
In fact this error is not due to sshfs but its ssh subsystem. Unlike ssh, sshfs does not give a very descriptive error in this case. The above error happens due to a possible security threat, namely the man-in-the-middle attack. If we know that the security has not been compromised then it is very likely that the RSA host key has been changed. The fix for the above error is very simple. All one has to do is to remove the cached host key from the ~/.ssh/known_hosts file. This post lists steps needed to get rid of the read: Connection reset by peer sshfs error.
Lets reproduce the error by running the following command from bash.
sshfs kamil@132.234.100.123:/home/florin /mnt/rec
The error message is produced.
read: Connection reset by peer
As mentioned in the introduction the actual error comes as part of inbuilt ssh security measure. To get a more descriptive error message ssh into the host in question instead of trying to sshfs mount one of its paths locally.
ssh kamil@132.234.100.123 echo blah
Using ssh produces the following error and terminates ssh session.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is 5c:0c:ab:ad:7b:32:c8:f3:b0:5d:4d:44:8c:9f:ef:93. Please contact your system administrator. Add correct host key in /home/florin/.ssh/known_hosts to get rid of this message. Offending key in /home/florin/.ssh/known_hosts:97 RSA host key for 132.234.100.123 has changed and you have requested strict checking. Host key verification failed.
The highlighted portion of the above warning tells us that the RSA host key on line 97 of the /home/kamil/.ssh/known_hosts file is the offender (it does not match the new credentials on the destination host). Ok, so lets get rid of line 97 of the /home/kamil/.ssh/known_hosts file.
sed -i -e '97d' /home/florin/.ssh/known_hosts
Done. Lets try the ssh again.
ssh kamil@132.234.100.123 echo foo bar
It now works just fine. Note that you will be asked to add the updated credentials to the /home/kamil/.ssh/known_hosts file.
The authenticity of host '132.234.100.123 (132.234.100.123)' can't be established. RSA key fingerprint is 5c:0c:ab:ad:7b:32:c8:f3:b0:5d:4d:44:8c:9f:ef:93. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '132.234.100.123' (RSA) to the list of known hosts. florin@132.234.100.123's password:
The sshfs should also work now.
sshfs kamil@132.234.100.123:/home/florin /mnt/rec
Running the above produces a password prompt and then ends with successful sshfs mount.
kamil@132.234.100.123's password:
Lets have a look what is now mounted.
mount
The highligted portion shows the sshfs mount worked.
...
proc on /proc type proc (rw)
sysfs on /sys type sysfs (rw)
devpts on /dev/pts type devpts (rw,gid=5,mode=620)
/dev/hda2 on /boot type ext2 (rw)
...
sshfs#kamil@132.234.100.123:/home/florin on /mnt/rec type fuse
(rw,nosuid,nodev,max_read=65536,user=kamila)
Hope this helps!
- powered by Verysign